Saturday Feb 14, 2026
Saturday Feb 14, 2026
Monday, 14 March 2016 00:00 - - {{hitsCtrl.values.hits}}

SISA Information Security Ltd. Cyber Security Researcher and Head – Business Development SAARC Region Nitin Bhatnagar
By Marianne David
 Q: As the threat of cybercrime grows exponentially across the globe, disrupting businesses along the way, could you outline where Sri Lanka stands in terms of strengths and weaknesses in combatting cybercrime?
Q: As the threat of cybercrime grows exponentially across the globe, disrupting businesses along the way, could you outline where Sri Lanka stands in terms of strengths and weaknesses in combatting cybercrime?
A: Comparing to the past few years, we see a drastic progress in the core understanding of cybersecurity-related subjects when discussed with the professionals working with various banking, telecom and other service providers in the country. We see a lot of initiatives taken by the Government such as setting up new Computer Crimes Division units to address computer-related crimes and also becoming the first country in South Asia to join the Budapest Cybercrime Convention, which is the only international treaty on cybercrimes globally.
In order to combat the cyber-crime we stress that organisations should report the incident faced directly to CERT (Computer Emergency Readiness Team) so that they can assist the organisation to recover from the cyber-attacks. This will also help CERT to formulate a roadmap for such incidents and it would be useful for others to follow so that they don’t fall victim. The CERT|CC (Computer Emergency Readiness Team | Co-ordination Centre) acts as the focal point for cybersecurity in Sri Lanka.
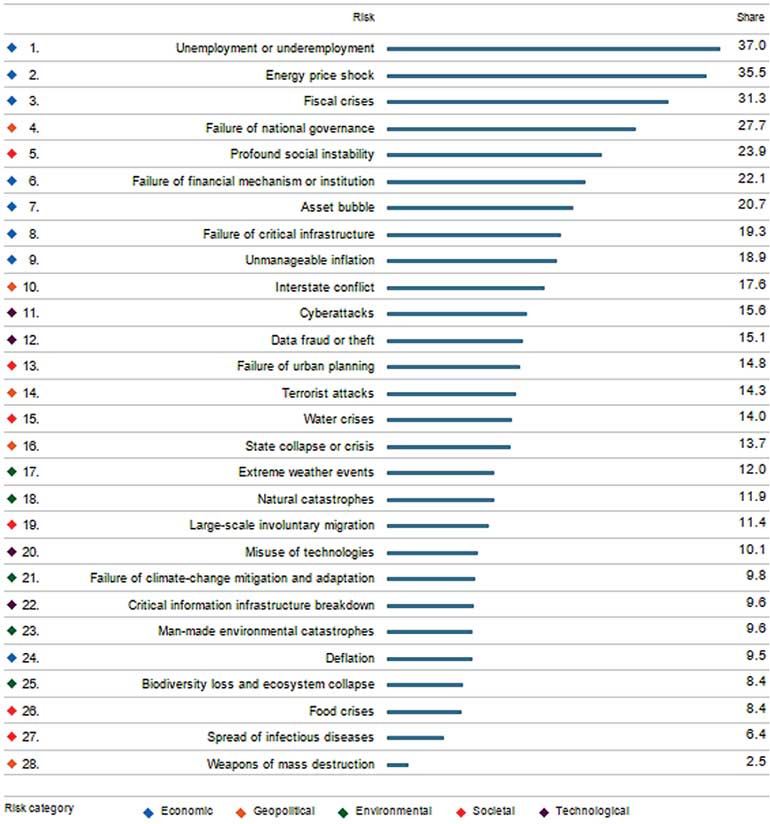
Cybercrimes will cost the global economy a whopping $445 billion this year as per the report from the World Economic Forum. Data fraud and theft and cyber-attacks rank among the top 10 threats in 140 economies with 15.1 % and 15.6% of share globally (attaining 11th and 12th ranks).
Sri Lanka has individually attained eighth rank and 19th rank for cyber-attacks and data theft and fraud respectively (with score 16 and 8) out of top 28 risks identified globally. (Reference URL http://reports.weforum.org/global-risks-2016/eos/#country/LKA).
Q: Credit/debit card fraud is a persistent threat; what steps need to be taken to minimise this?
A: Let us try to understand how one can fall prey to credit/debit card fraud:
nSkimming: This type of card fraud happens during a seemingly legitimate transaction, for example when paying for goods or service at a restaurant/petrol pump or withdrawing money from a cash machine. By putting your card into an electronic device before making the transaction (by a dishonest employee) and skimming your card at a cash machine, criminals obtain your card details, which allows them to use them for their own purchases and transactions.
nPhishing: Many criminals obtain card details from cardholders themselves by tricking them into revealing sensitive information. Usually, the criminals pretend to be bank staff or the police, asking for card details such as passwords, PINs, account numbers, etc. for ‘security reasons’.
 While we are not leaving any stone unturned in improving defences, payment card data continues to be a target for criminals around the world. Steps that organisations need to take in order to minimise the risk of getting compromised – we need to have strong security training programs that must address people, process and technology.
While we are not leaving any stone unturned in improving defences, payment card data continues to be a target for criminals around the world. Steps that organisations need to take in order to minimise the risk of getting compromised – we need to have strong security training programs that must address people, process and technology.
Q: What are the international security standards that organisations should be following to combat such cyber-crimes and card frauds?
A: We need to follow these international security standards:
1. PCI Suite which includes PCI-DSS, PA-DSS, PCI-PIN and PCI-P2PE to protect organisations from being victimised by attackers.
2. ISO/IEC 27001 (ISO 27001:2013) which is focused on Information Security Management System.
Q: How important is regulation?
A: Last year in October 2015 we saw the New York Stock Exchange (NYSE) release a guide to cybersecurity written by 80 individual contributors. In this ISO/IEC 27001 has been identified as a most comprehensive security standard and a good choice for any size of organisation because it is respected globally and is the one of the most commonly mapped against other security standards. ISO/IEC 27001 can help any organisation with a best-practice cybersecurity posture. ISMS addresses people, processes, and technology, providing an enterprise-wide approach to protecting information.
ISO/IEC 27001 (ISO 27001:2013) has been also mandated by the Central Bank of Sri Lanka, whereas PCI-DSS has been mandated by the payment brands (VISA, MasterCard, Amex, JCB and Discover). We need to have the Central Bank take an extra step to enforce the PCI DSS regulation in order to protect against card frauds.
Reserve Bank of India (RBI) has mandated Indian banks/financial institutions and large merchants with IP traffic to be PCI-DSS compliant. Similarly, Saudi Arabian Monetary Agency (SAMA) – Saudi Arabia has adopted the Payment Card Industry Data Security Standard (PCI DSS) for high level of payment card protection and data secrecy of payment card operations within the country.
Q: What is the most important thing a company could do right now to protect itself from cybercrime and what would you identify as the most important preventive measures?
A: In order to be protected from cybercrime, organisations should understand the importance of having a proper information security framework for their organisation based on the kind of business that they are into. Organisations on a broader level need to get the highest level of sponsorship and right team/person for the information security program within the organisation, have a proper project plan and budget sufficient time to get it right. Also important is creation of a cross-functional PCI Steering Committee for PCI-DSS (protection against card fraud) related project as well as creation of other relevant steering committees for security standards like ISO27001 and Privacy Standard – BS 10012 and last but not the least conduct yearly risk assessments for your environment.
The basic parameters that organisations should consider inhabiting to their employees are:
Q: What can individuals do to protect themselves from falling prey?
A: Let us try to understand how one can fall prey to cyber-attacks. Common cyber threats faced worldwide are:
Common cybercrime which can happen with common man:
1. Cyber bullying
Cyber bullying is the most common fear in teenagers’ eyes. It has become common over the past five years; generally those from the age below 18 are more susceptible and fear cyber bullying. Cyber bullying is when a person receives threats, negative comments or negative pictures or comments from other person which are distressing. Teenage females fear cyber-crime the most. In my analysis generally a person who is affected can become depressed, or feel humiliated and threatened. Through this analysis we have realised that if a person is bullied online, he or she may be depressed to the extent of resorting to self-harm.
2. Financial frauds
Fraudsters/hackers can contact their potential victims through various means, such as face-to-face interaction, by post, phone calls, SMS and/or emails. It is very difficult to check identities and legitimacy of individuals and companies. Fraudsters can divert visitors to dummy sites and steal personal financial information, such as credit/debit card information, account details and other personally identified information.
3. Identity theft
Identity theft is a form of stealing someone’s identity in which someone pretends to be someone else by assuming that person’s identity, usually as a method to gain access to other benefits in that person’s name. Identity theft occurs when someone uses another’s personally identifying information, like their name, PAN, voter ID, passport, Aadhaar card or credit/debit card number, without their permission, to commit fraud or other crimes.
4. Cyber stalking
Cyber stalking is the use of the internet or other electronic means to harass an individual, a group, or an organisation. It may include false allegations and defamation. It may also include identity theft, sabotage and solicitation for sex, or gathering information that may be used to threaten or harass.
5. Phishing
Phishing is the attempt to acquire sensitive personal information such as usernames, passwords, and credit/debit card details by masquerading as a trustworthy entity in an electronic communication. Communications declaring to be from popular social websites, auction sites, banks, online payment processors or IT administrators are commonly used to lure unsuspecting public. Phishing emails may contain links to websites that are infected with malware. Steps that individuals have to take to protect the card information are they should have a strong internet banking password, one should memorise the ATM PIN and CVV (avoid writing down at the back of the card) and using internet banking or doing any financial transaction at cyber cafés should be avoided. Once should never disclose card details to anyone, including your bank staff; destroy all documents including receipts that contain information about your card or account, shop at secure online stores, and check your bank statements on a regular basis to make sure all transactions were made by you.
Q: How real is the threat of data skimming and how can it be countered?
A: Card skimming fraud happens during a seemingly legitimate transaction, for example when paying for goods or service at a restaurant/petrol pump or withdrawing money from a cash machine. By putting your card into an electronic device before making the transaction (by a dishonest employee) and skimming your card at a cash machine, criminals obtain your card details which allows them to use them for their own purchases and transactions.
Skimmers can be distressing. It would be good if one can visit only ATMs that are in well-lit and public areas, and to be aware of your surroundings as you approach the cash machine. If you visit a cash machine that looks strange, tampered with, or out of place, then try to find another ATM.
Q: Could you outline SISA’s operations and how it protects companies from these threats?
A: SISA is a payment security specialist company and amongst the first PCI QSA in SAARC region and a market leader in information security domain. It has a customer footprint in 40 countries for consulting, training and solutions. SISA is the only company to offer synergistic security model –that is the Combination of services, training and automation – that improves security posture but at the same time reduces total cost of security. SISA works with banks, payment processors, payment application service providers and financial institutions to support them in complying with the PCI-DSS standard [Payment Card Industry Data Security Standard (PCI DSS)] and certification.