Tuesday Feb 17, 2026
Tuesday Feb 17, 2026
Wednesday, 10 August 2016 00:02 - - {{hitsCtrl.values.hits}}

By Hiyal Biyagamage
 The CEO Forum of the EC-Council Cyber Security Summit was held on Monday and discussed the impact of insider threats which leads to disastrous cyber security conflicts within an organisation. The CEO Forum which happened on the sidelines of the coveted Cyber Security Summit 2016 had a panel which consisted experienced personnel who represent the cyber security sphere. The panel was moderated by Daily FT Editor Nisthar Cassim.
The CEO Forum of the EC-Council Cyber Security Summit was held on Monday and discussed the impact of insider threats which leads to disastrous cyber security conflicts within an organisation. The CEO Forum which happened on the sidelines of the coveted Cyber Security Summit 2016 had a panel which consisted experienced personnel who represent the cyber security sphere. The panel was moderated by Daily FT Editor Nisthar Cassim.
Cyber security: A C-suite issue
Starting the conversation, Asia Policy Partners LLC, Hong Kong Managing Partner Michael Mudd said that cyber security does no longer sit in the back end of a business process.
“As a CEO, you don’t want to get memos or hear about cyber security intrusions. Cyber security is not an IT issue; it is a C-suite issue. It is front and centre stage for every company out there, especially for larger enterprises. Some of you may have heard about the hack which happened two years back in US. 40 million credit card records were stolen and costs are still to be determined. Chief IT security officer got fired, CIO got fired and then the board fired the CEO as well. Not funny though; half of the board members were pressurised to tend to their resignation.”
“Cyber security does no longer sit in the back end of IT or your business process. It is very front and forward. In US, moves are being taken to combat this legally. There has been a proposal this year for an amendment to the Cyber Security Disclosure Act of 2015 which addresses cyber security monitor awareness by the board. What this means is that every public-listed company in the US must have a member in their board to take on responsibility to cyber security issues.
“What does that mean for the rest of the world? If you deal with a US company, they are going to ask what you are doing about your cyber security because they do not want to get compromised by your company as a customer or a supplier. If you look at the credit card fraud, it was the supplier who introduced a malware to the data centre which allowed cyber criminals to steal credit card 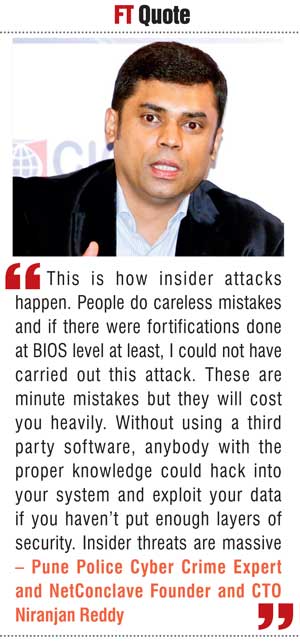 records. The biggest problem was that all the records were stolen three weeks back before it was found out,” said Mudd.
records. The biggest problem was that all the records were stolen three weeks back before it was found out,” said Mudd.
Hacking with a bootable USB
Pune Police Cyber Crime Expert and NetConclave Founder and CTO Niranjan Reddy did a demo on how a laptop with Windows could be hacked easily. He did not use any third party software; all he had was a bootable USB drive where he used several commands in the Command Prompt to change the user privileges to hack into the system.
“This is how insider attacks happen. People do careless mistakes and if there were fortifications done at BIOS level at least, I could not have carried out this attack. These are minute mistakes but they will cost you heavily. Without using a third party software, anybody with the proper knowledge could hack into your system and exploit your data if you haven’t put enough layers of security. Insider threats are massive,” said Reddy.
Putting down a sound cyber policy
Office of the Council of Europe, Romania Project Manager Cyber Crime program Dr. Matteo Lucchetti shared his experiences on how banks in Europe faced cyber security attacks.
“I did work for a famous bank in Italy and attention towards insider threats was very high. One of the most recent threats we have experienced was of an email sent out by a forged account pretending to be the CEO, to the company CFO or someone from the financial department. The email asked for immediate transfer of funds, leveraging on the trust between the CEO and the CFO, circumventing internal procedures and policies. Although it seems almost incredible that an attack of this nature can go through, it has proven to be as simple as effective.”
“Statistics show that similar kind of attacks went through and already costed tens of million Euros in European Union only. To go through such attacks, there should be an insider who tells their peers when to deliver the attack. In the banking sector in EU, all of these threats are usually addressed with a risk-based approach. Although there is no silver bullet capable of assuring full protection, implementing sounding risk management policies allows to measure the level of exposure and to design suitable strategies to mitigate the relevant risks", said Dr. Matteo.
He also expressed his views about sharing information between organisations during a disastrous attack.
“Private sector companies should not consider cyber threats as a competitive filed. This is a very old concept but it is something that needs to be remarked. There is a big reluctance within private sector companies to cooperate with the competitor to figure out different cyber threats. The conception is that I should not help my competitor to identify these threats but I should always help the community. Information sharing will help companies to take more appropriate counter measures to many of the attacks.”
Security is a valuable opportunity
 CISCO Head of Security Sales, India and SAARC Pravin Srinivasan emphasised on how security has become very complicated in an era of digitisation.
CISCO Head of Security Sales, India and SAARC Pravin Srinivasan emphasised on how security has become very complicated in an era of digitisation.
“A lot of companies talk about digitisation which has become critical. Companies putting every record in the web and manufacturing companies rely on IoT and they connect their machines into ERP systems. Public sector also lends services electronically. These scenarios mean that certain things are happening by default. Data are going to the cloud and people are busy with smart devices. What happens here is that attacks surface to such an extent where we are starting to see these attacks a lot more.”
“Cyber threats have been always a C-suite issue; only difference right now is that with the involvement in digitisation process, threats have become a certain roadblock for the top management. If the Government puts a lot of data in the web and it gets hacked; it must have put a million lives at stake. One of the ways we could look at this is that because these projects have become so critical to the company as a whole; adding security should be a regular process from day one. Before we start thinking about implementing an application, let us first see how we can make it safer. That is an opportunity we have,” he said.
Srinivasan also said that pretty much every threat many companies face right now are insider threats. “The threat may come from outside but ultimately, the inside source will cause lot more damage. It could happen with the knowledge of the insider or without the knowledge of the insider,” Srinivasan pointed out.
A gap in human resources
Speaking at the panel, Deakin University Australia Centre for Cyber Security Research Deputy Director Prof. Matthew Warren made a valid point by saying that the difficulty to find qualified cyber professionals is causing numerous problems for many organisations.
“In terms of the incidents that have been discussed and when you put them into a business context, one of the issues is the consequences of these attacks. When media record these incidents, it will start to impact the brand of your organisation. Shareholders will start to worry about your company, they would lose confidence and the stock market will start to react. Customers will leave your company and go to a competitor. All of a sudden, you have a situation where a security issue starts to make your life very unpleasant.”
“It may not be just a simple insider issue but it could have been something wrong with the human aspect. Studies have unravelled that complexity of the technology within an organisation has prompted insiders to direct a cyber-attack. If you take a look at some stats; CISCO publically told the Australian Government that there is a global shortage of a million cyber security specialists and professionals. Symantec CTO also revealed that by the year 2019, there is going to be about a 17 million shortage of cyber security professionals. So in terms of human resources, cyber security is becoming a huge issue. Companies are finding it hard to acquire  skilled employees to protect their systems.”
skilled employees to protect their systems.”
The disgruntled employee
CICRA Holdings Director/CEO Boshan Dayaratne gave a small insight into the local scene of cyber security malpractices at the panel discussion.
“We have done a lot of projects in Sri Lanka and we see insider threat is quite at large. There are disgruntled employees who do not want to leave the company. There are people who plan to leave the organisation but the management would not know until they give their resignation. Both types take your intellectual property out and also confidential information out of the organisation, even before they give the resignation.
“That is a major fact we are witnessing in Sri Lanka and I think it is the same in other parts of the world as well. In some cases, you get certain viruses into your system due to your poor knowledge of security. Without people knowing, there are data being transmitted outside. Your computer could be a bot. We all focus on external threats but we are less focused about our internal threats. One research states that 90% of external attacks happen because of insiders,” said Dayaratne.
The panellists were asked a few questions at the forum. Below are some of them:
Q: How late would companies get to know that they have been attacked?
Praveen: That evidence is quite scary. If you analyse multiple reports, the average time taken for companies to figure out they have been attacked is six to eight months. The time taken out to clean the infection will be a year or more. If you take a well-written malware and analyse its time of execution; it would steal your data within six to eight hours. There is a quantum jump in that and it is creating so many problems for organisations.
A lot of companies do realise that their company has been hacked only when they see their data in a public domain. When your house gets robbed, the thieves will not leave any traces. Finding advanced threats are becoming more and more difficult.
Q: How does the financial sector gets affected due to these cyber-attacks?
Michael: We learnt a lot from the recent Bangladesh bank heist and this was not the first. It is quite hard to determine when there was a first. There are certain indications that there could be an Asian stake behind this that hired a gang to do the job. Banks of course store an enormous amount of data so they need cyber defences.
One of the issues has been that the history of banking software; there are still legacy systems. They were never designed to deliver  modern components like internet banking or mobile banking. These implementations have been always difficult with legacy systems. The proven truth is getting bigger and the state of attacks surface much faster. Cyber attackers nowadays don’t necessarily go after the top 10 banks in the world but they are aiming small banks because they are less fortified.
modern components like internet banking or mobile banking. These implementations have been always difficult with legacy systems. The proven truth is getting bigger and the state of attacks surface much faster. Cyber attackers nowadays don’t necessarily go after the top 10 banks in the world but they are aiming small banks because they are less fortified.
Q: We are living in this new era of technology. Is it safer to go back to the era of bows and arrows? Because, everything you create today has something else coming up tomorrow. We feel we are not safe. Where do we go?
Praveen: I think the fundamental approach needs to be changed. Security as an afterthought is no longer there but security as a post-deployment scenario is a welcomed approach. That is where we need to create a lot of awareness. Whenever we launch any new technology, the security build-up needs to be done from the lowest level. You will never be 100% secured but the fact is that when you know that you are not 100% secured; you tend to be more careful and look for any loopholes that would cause any sort of intrusion.
Niranjan: Security is an investment. We have technologies and if we want to go back to the old era, you might have to do lot more things again. You have fast-paced technologies right now so I guess it would be easier to execute a strategy now. You can’t make anything secure but you can take a proactive approach. When you are building an app, you could do threat modelling. As you are developing it, look at some security perspectives and keep on doing regular audits. You should also have a layered defence approach which means having different layers of technology. You should not have a single firewall and say I am secured now. You 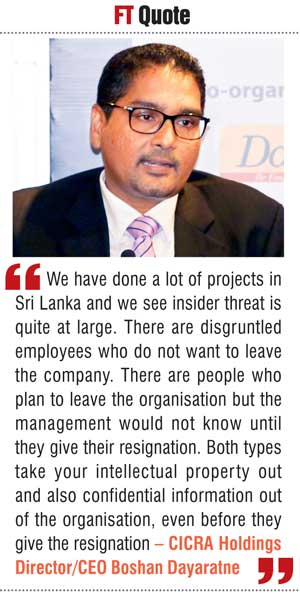 always have to make it difficult for the hackers to exploit your data but coming back, no company could perform a 100% security assessment.
always have to make it difficult for the hackers to exploit your data but coming back, no company could perform a 100% security assessment.
Q: What are the most recent threats that have surfaced during the last year or so?
Niranjan: Ransomware is pretty big. Hackers will lock your system with a high bit encryption and keep you at ransom. To unlock your system, you have to pay a huge amount to the hackers. It is on the rise.
Brian Kealy of Microsoft: I think the conversation we are having right now is largely based on risk management. When you talk about ransomware, Zero Day or DDoS or anything else; smart, matured organisations manage risks of all sorts. Cyber security is a type of risk and if you could face it with right controls around you, mitigating cyber threats is not quite an issue. In this conversation, some of the time we are losing the side of the fact that it is just another form of a risk and it is not a new thing for a board to manage but on the other side, boards are managing productivity.
So how do I make my organisation more productive, do more with less and make it more effective? Technology will enable that like any other form of mechanisation for the last 1,000 years of business. Technology is less well known by most boards but the opportunity and the risk need to be weighed together. I think we need to strike a balance between these two.
The EC-Council Cyber Security Summit 2016 is co-organised by CICRA Holdings – Sri Lanka’s pioneering cyber security training and consultancy provider – and Daily FT.
Supported by the ICT Agency, the strategic partners of the 2016 Cyber Security Summit were Microsoft and CISCO, the electronic payment gateway was LankaPay, the insurance partner was Sri Lanka Insurance, the creative partner was BBDO Lanka, the printing partner was OfficeMax, the hospitality partner was Cinnamon Lakeside and the electronic media partner was MTV and MBC Radio. Deakin University and EPIC Lanka also extended their support to the Summit.
Pix by Daminda Harsha Perera





