Saturday Feb 21, 2026
Saturday Feb 21, 2026
Wednesday, 9 October 2019 00:00 - - {{hitsCtrl.values.hits}}
Several print media reports published in early April 2019 referred to some apprehensive details from the 24th edition of Microsoft’s Security Intelligence Report comprising of core insights and key trends derived by sifting through data between January to December 2018 from multiple, diverse sources, including 6.5 trillion threat signals that go through the Microsoft cloud system every day.
This report is a reflection on the previous security events and includes an overview of the security landscape, lessons learned from the field, and recommended best practices.
As mentioned by the Microsoft Country Manager for Sri Lanka and Maldives, “Undoubtedly, cybersecurity is one of the most pressing issues for organisations today. As cyber attacks continue to increase in frequency and sophistication, understanding prevalent cyber threats and how to limit their impact has become an imperative.”
The report also revealed that Sri Lanka was among the most vulnerable to ‘malware’ which causes risks for organisations and individuals in the form of impaired usability, data loss, intellectual property theft, monetary loss, emotional distress and can even put human life at risk. Whilst the global malware encounter rate has decreased by 34%, the malware encounter in Sri Lanka was 109% more than the global average, highlighting the correlation of infection rates with human development factors and technology readiness within a society.
The report also found that the Asia Pacific markets with the lowest malware encounter rates are Japan, Australia and New Zealand. These locations tend to have mature cyber security infrastructures in place and well established programs for protecting critical infrastructure and communicating such best practices to the citizens.
According to a statement issued by a Sri Lankan Computer Emergency Readiness Team, five websites on an average in Sri Lanka are hacked per day. Apparently, there are number of reasons why hackers may vandalise a website, which can either be to mock the site, the government or both at the same time and make their mark on it. However, this is the least of the problems, because, these hackers also take down pages and expose its contents to competitors!
In view of growing attacks here, online security threats and social media related incidents, the government has enacted, a Cyber Security Bill to provide critical information infrastructure within Sri Lanka. The Act gives sweeping powers to state cyber agencies and institutions and the Digital Infrastructure and Information Ministry, despite concerns from civil liberties activists and computer societies over judicial oversight and potential abuse of power. Alongside the new disposition on terrorism-related content, the Act seeks to set a framework to prevent the misuse of digital devices including social media networks, they said.
This statute provides for the establishment of the Cyber Security Agency (CSA) the empowerment of the Sri Lanka Computer Emergency Readiness Team (CERT) and the proposed National Cyber Security Agency with responsibility for all cyber security activities. This will ensure the effective implementation of the National Cyber Security Strategy in Sri Lanka to prevent, mitigate and respond to cyber security threats and incidents effectively and efficiently.
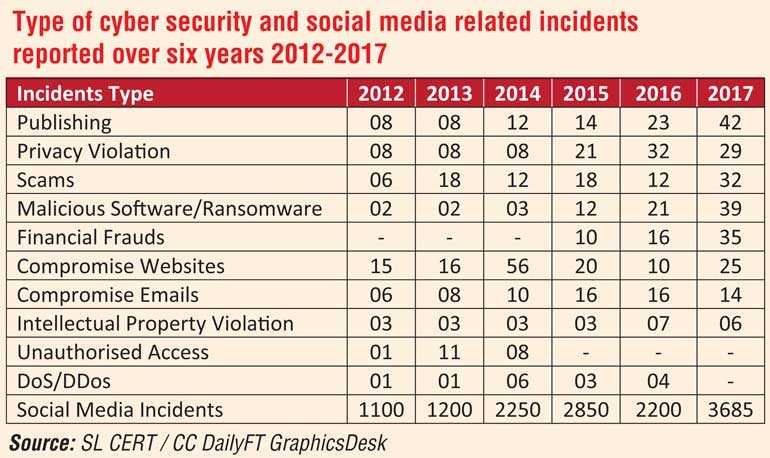
The aforesaid steps are by no way a means to an end but, certainly a very meaningful beginning towards meeting the rapid steps in technology advances that one sees from day to day but all the same, the implementation of which must be treated with a sense of urgency as Cyber crime in this country seems to be taking a serious upward turn. Looking at the past five years from 2012 to 2017, set out in the given diagram, are some interesting statistics provided by courtesy of the Daily FT recently published, which provides some interesting reading.
It is believed that, since of late the position has been even more acute. What has been stated above are some facts obtained from widely published information which will give you some indication of how the consequences of cyber crime could well undermine both business and personal interests perhaps to an irreversible extent.
In mid-July 2019, the print media disclosed that there had been a data breach at British Airways, where details of about 500,000 customers had been hacked by what was described as a ‘sophisticated malicious criminal attack’ on its website. This incident was first disclosed by BA on 6 September 2018 and they are now facing a record fine of GBP 183 million imposed by the Information Commissioners Office (ICO) which is the British governments ‘watchdog’ over such events. The General Data Protection Regulation (GDPR) came into force in Britain last year and was the biggest shake up of data privacy in 20 years.
It is of interest to add that the Information Commissioner in Britain, went on to state that “People’s personal data is just that – personal! When an organisation fails to protect it from loss, damage or theft, it is more than an inconvenience. That’s why the law is clear-when you are entrusted with personal data, you must look after it. Those that don’t will face scrutiny from my office to check that they have taken appropriate steps to protect fundamental privacy rights”. The UK ‘watchdog’ proposes also to fine Marriott International Inc. a sum of $ 124 million for data breach. The enormity of the risk that faces business interests worldwide is further illustrated by a report from Reuters dated 22 July 2019 which gives details of seven of the biggest US data breach settlements in recent times, as follows:
1) Equifax
Following its 2017 data breach, Equifax will pay up to $ 700 million to the US Federal Trade Commission, the Consumer Financial Protection Bureau and nearly all US states and territories. That includes a $ 175 million fine to the states and $ 100 million to the CFPB. It will also establish a $ 300 million restitution fund for harmed consumers. That amount could grow to $ 425 million depending on how many consumers act on it.
2) Uber
In 2018, ride-hailing app Uber reached a $ 148 million settlement with 50 US states and Washington, DC, for failing to disclose a massive data breach in 2016. It exposed personal data from 57 million user accounts.
3) Target
Retailer Target Corp agreed in 2017 to pay $ 18.5 million to 47 US states and the District of Columbia for the company’s massive 2013 data breach. Target reported that hackers stole data from up to 40 million credit and debit cards from shoppers who visited its stores in the 2013 holiday season.
4) Anthem
Anthem, Inc. agreed to pay $ 16 million to the US Department of Health and Human Services and the Office for Civil Rights in 2018 to settle potential violations of HIPAA, the Health Insurance Portability and Accountability Act Privacy and Security Rules, an HHS statement said. A series of cyber attacks exposed the health information of almost 79 million people.
5) Premera
Earlier this month, health insurance company Premera Blue Cross agreed to pay $ 10 million to 30 US states for allegedly failing to secure consumer data. A hacker had access to its network of private health information and Social Security numbers from May 2014 to March 2015, a statement from the Washington state attorney general said.
6) Nationwide Mutual
Insurance company Nationwide Mutual agreed in 2017 to pay $ 5.5 million to 33 US states for a 2012 data breach. The Attorney General alleged that the company failed to apply a critical security patch and resulted in the loss of the personal information of over one million consumers.
7) Ashley Madison
Adultery website Ashley Madison’s parent company Ruby Corp agreed in 2016 to pay $ 1.6 million to settle FTC and state charges that it failed to protect 36 million users’ account and profile information in a July 2015 data breach. In a separate 2017 settlement, the company agreed to pay $ 11.2 million in a class-action settlement, which said users with valid claims could recoup up to $ 3,500 depending on their losses from the breach.
According to the outcome of a study carried out recently in the United States, cyber-attacks in 2018, largely by way of ransomware has cost around $ 45 billion in losses worldwide!
Yet another alarming development that has now come into focus is Business email compromise (BEC) as the top cause of loss by cyber claims followed by ransomware, which is becoming increasingly targeted and disruptive, affecting business interruption costs. According to AIG, BEC has entered the report in 2019, under a new category given the high number of such claims received by AIG over the past 12 months.
In most cases the compromise can be traced back to a phishing email containing a link or attachment. If the recipient engages with the content of a phishing email it may allow intrusion into the user’s inbox. The majority of users are familiar with the concept of phishing emails but there remains a high number of incidents where the user follows a link directing the recipient to a bogus login screen. As soon as the victim enters their credentials, they are captured by the cyber-criminal who then has the necessary information to login to the victim’s email account.
The perpetrator is then able to send and receive emails from the victim’s email address and access all the information in the victim’s email inbox. In many cases the BEC is exacerbated by malware that spreads the scam to contacts in the recipient’s inbox. A relatively simple type of scam, is where BEC attackers often target individuals responsible for sending payments, using spoof accounts to impersonate the company C-suite or a supplier and requesting money transfers, tax records and/or other sensitive data.
Other attacks focus on the content of the recipient’s inbox, harvesting client and employee information, including personal data. They may also target confidential corporate information, including trade secrets, but most are motivated by monetary gain.
“Ultimately what’s behind a lot of these compromises is organised crime,” says Jonathan Ball, partner at Norton Rose Fulbright. “They’re not interested in stealing personal data and selling it on the dark web. It’s pure financial fraud.”
BEC attacks are often successful because they use social engineering to create emails that appear legitimate. Even larger organisations may fall for the scams, explains Jose Martinez, vice president of financial lines major loss claims, EMEA, AIG, suggesting more investment is needed to train staff to better identify rogue messages. “We’re still seeing a surprisingly high level of these forms of fraud being perpetrated and some are affecting quite large and sophisticated clients. You may think that every CFO at a large company would know about this by now, but it’s still happening.”
Although financial services firms were the first buyers of cyber insurance and the largest sector, we saw professional services firms move ahead in 2018 in the number of reported claims. This is also the sector most vulnerable to business email compromise. Year-on-year, the number of claims emanating from professional services firms, including law firms and accountants, increased from 18% to 22%.
Such firms may be more prone to BEC because of a lack of sophistication when it comes to cyber security, whereas in the case of financial services firms, as they are generally regulated heavily, there are better controls in place compared with other sectors including professional services.
Where Sri Lanka is concerned, there are three specialised servicing units, directly under the Ministry of the Digital Infrastructure and Information Technology as follows:
Sri Lanka CERT (Computer Emergency Readiness Team Co-ordination Centre)
The Computer Emergency Response Teams (CERTs)
Financial Sector Computer Security Incident Response Team (FINCSIRT)
These units are expected to respond suitably to computer security alerts and incidents affecting banks and other licensed financial institutions. Currently, it could be said that these units operate more or less independently, but co-ordination is an essential ingredient to meet the looming security threat facing the country from cyber-attacks.
Obviously, innovation is very necessary if a business is to thrive in the prevailing environment as so aptly enunciated by David Bowcott of AON who said, “The role that risk transfer plays in helping propel today’s innovation is similar to the role it played when ships were sailing to new worlds. Modern insurance was born out of a coffee house in London for maritime traders to protect their voyages. Risk transfer – however it evolves over time – plays a key role in giving people the confidence to move into new industries, new ways of doing business, and sometimes, entirely new worlds.”
The more recent information coming to hand indicates that reported data breaches in the six months of 2019 compared to mid-year 2018 is believed to be the worst such period on record Eight breaches alone had exposed more than 3.2 billion records. Then again in July 2019 Capital One in the US experienced a mega data breach where a hacker stole data of around 100 million people in the US alone and an additional 6 million in Canada, which was held on Capital One’s cloud server. This information had come mainly from consumer and small business applications for Credit Cards filled out between 2005 and early 2019 and included date of birth, income social security nos., linked bank account nos. for secured credit cards including 1 million social security nos. for Canadian customers.
On the other side of the coin, it is of interest to mention, an article published in the local print media on 28 August 2019 reported that in the UK a hacker had been arrested and ordered to pay compensation to affected parties is a sum of GBP 922,000.00, plus of course a jail term of 10 years and 8 months. He had used phishing email scams to obtain the financial data of tens of thousands customers and used this information in various way and methods to make substantial financial gains. This is of course a rare instance, where not only was the hacker identified but ordered to compensate those affected.
The gist of the message here is that there is available in the market a risk transfer mechanism by way of ‘Digital Business & Data Protection Insurance’. Such insurance cover is designed to mitigate losses from the variety of cyber incidents including Data Breaches, Business Interruption and Network Damages.
Generally speaking, such a policy is in three sections covering:
Own Damage covers;
Third Party covers;
Covers Defence Costs for Regulatory Proceedings and Fines and Penalties
Pricing for this product depends on various factors, some of which, are listed below;
In conclusion, it is of interest to add that, a Digital Infrastructure Ministry Committee has now released a draft framework for a Personal Data Protection Bill, a law it is hoping to push through by October this year. Among other things, it will give someone the right to know who holds his or her personal information, from supermarket loyalty programs to other private companies and Government bodies.