Friday Feb 13, 2026
Friday Feb 13, 2026
Thursday, 6 September 2018 00:00 - - {{hitsCtrl.values.hits}}
By Nisa Vithana
Undoubtedly technology has become a daily part of our lives, and to be honest sometimes we feel a bit overwhelmed by it. Every morning we wake up to our devices, “What have I missed while I was sleeping through the night. Should I check my messages, Facebook notifications, LinkedIn NewsFeed, Twitter feed, where should I post my morning selfie, Instagram or Snapchat and how does snapchat work anyway?”
We often contemplate about these thoughts during the day, and if we can find time in between, some of us work for a living too. We often check bank balances online, purchase our favourite pair of shoes by using the credit card, and fill that e-registration form of the hotel that we are planning to spend the holiday, or enter our personal information on number of online forms while browsing the internet. These are only a few things that we deal with whilst interacting with technology. Whether we like it or not almost everything has become digitised and every day we struggle to keep up with the constant advancement in technology.
Have you ever been a victim of a cyber-attack or have you not even heard of that word? Most of us who own an e-mail address have become a victim of a data breach at least once in our lifetime. The moment you receive a promotional email from a vendor whom you did not subscribe or you see a discount of an item of a site you just visited, receive a suggestion for your next purchase, unknowingly you’ve exposed your sensitive, protected or confidential information to a system owner.
What is sensitive data?
Predominantly, our whole life revolves around data. Once we are born to this world our biological information such as organs, cells tissues, blood type and all physical materials from human body are identified. Then we’ve been given a name as an identification, given an identification number and as per our biological characteristics we’ve been allocated to a social group. Eventually we create our own internet identity such as an e-mail address, FB account, twitter, Instagram, LinkedIn and the list goes on. Simultaneously we build our own psychological identity such as qualities, beliefs, personality, expressions which relates to our self-image, self-esteem and individuality. A combination of these characteristics allows an individual to appear unique as an identifiable person.
Every day we use these information to mark our presence, get things done, make our own decisions and for our physical well-being. We all have our own set of personal information which we don’t want to disclose due to various personal reasons. Whether you are a top-notch CEO of a fortune 500 company or a farmer who owns fields in a tiny tropical island, your personal information is your identity. Organisations today collect huge amounts of information from their stakeholders. Creating a social networking account has no difference in creating a bank account or registering for an online degree or fill up a bio-data. Assume those key pieces of your personal information are stolen from you and perhaps shared with criminals and used for illegal activities to impersonate you, how would you feel?
By law, sensitive data refers to personally identifiable information such as racial and ethnic origin, philosophical and religious, political opinions, biometric and genetic information, sexual orientation or any data concerning to health of a natural living person that must be protected from unauthorised access. Be it an individual or an organisation, access to sensitive data must be safeguarded for various legal and ethical reasons and for issues pertaining to your personal privacy or proprietary considerations.
How to protect your sensitive data?
Over the last few years with the rapid development of technology, the importance of data protection increased at an unprecedented rate. Organisations collect, store and process more information on individuals than ever before. People invest on safeguarding physical assets such as money, property and vehicles, thus leaving most important personal data unattended.
Encrypt data on your devices
Most of us have some kind of sensitive information on the technological devices we use. We store passwords, photos, bank details, email addresses, contact details, medical information and sometimes IP addresses in these devices. Computer systems and networks need protection against hackers and attackers. Securing your devices and computer networks are one way to protect your sensitive data. Sensitive data on portable devices such as mobile phones can be password protected and encrypted for security and privacy reasons. Data encryption translates your information into code form which only people with the secret key (decryption key or password) can have access and read it. You can also add extra security by using two-factor authentication to protect your privacy. Always keep your devices up-to-date with appropriate security software. Before you dispose your old devices be sure to wipe off all your personal information from its memory.
Protect privacy on social media
Most social networking websites collect your personal information through various automated means. There are a number of simple ways to protect your privacy in social media. The next thing you will do after creating your profile on social media is adding connections. Be selective with friend requests, be cautious with your identity card number or credit/debit card information, always use strong passwords and two-factor authentication. Provide difficult to guess information for security questions on social media websites. Click on third party links with caution.
Read and understand privacy policy of website
For convenience purposes there are a number of online web service platforms we use on a day-to-day basis. Paying utilities, managing bank accounts, booking airline tickets, movie tickets, holiday packages have been easier than ever before due to the technological advancement lately and save us time and money tremendously. But, do you know that free online services use your data to make money for themselves? The moment you enter your personal sensitive data on a free website, you trade your information for the free service you experience.
This type of exchange can affect your privacy. The more they know about you, the more power they can have over you. These websites will then trade your information with third parties or their strategic partners who is then going to influence your decisions and shapes of your behaviour. It is important to know who you share your information with. Always read privacy policies of such websites. Although they can be long and complex it gives you information as to how the site maintains its accuracy, security and the way they process and control collected information. It will also tell you whether or not they will share information with third parties. Next time when you decide to enter your personal data on such websites, see if you can understand the site’s privacy policy and if you don’t see one, consider doing business elsewhere!
Be alert when disclosing your financial data
In general, be alert of possible impersonators. Identity theft happens in all parts of the world and it’s becoming complex and serious. Be cautious about with whom you share your personal and financial information. Do not disclose your personal information and whereabouts by email or over the internet unless you know who you are dealing with.
Why information Security matters?
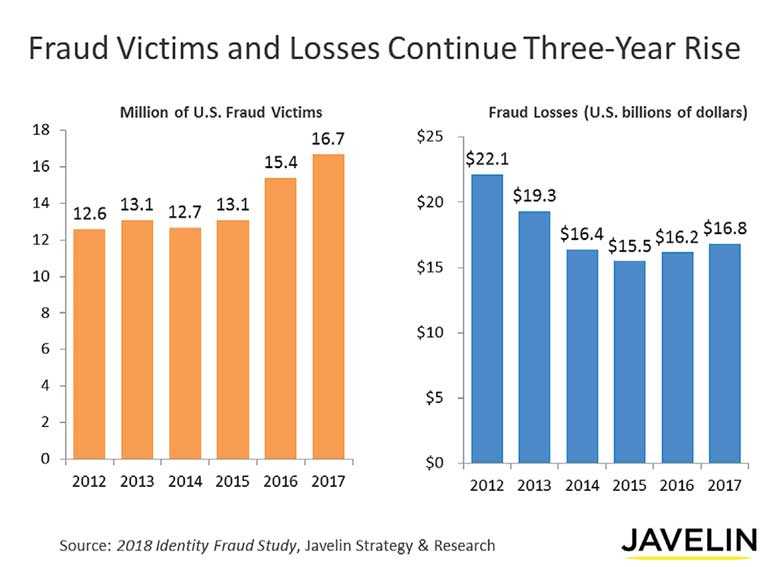
Information Security or in other words Cybersecurity has become a major concern around the world lately. It is discussed not only by the techies but also at national levels as a serious threat to the human wellbeing. A research based advisory firm Javelin Strategy and Research in their latest report revealed that the number of identity fraud victims increased by 8% in the US alone in 2017 with fraud losses amounting $ 16.8 billion.
How can you protect yourself from identity fraud?
Practice good online security habits. Avoid using public Wi-Fi, protect yourself from unauthorised transactions by turning on notification alerts on suspicious activity of your social accounts, bank accounts and emails. Moreover, be smart and alert!
(The writer is the Program Manager at SHe CISO Exec. Foundation UK and Sri Lanka.)