
Apple’s annual product releases attract a frenzy of attention. But this year as curious fans logged onto social media to weigh in on the newly released iPhone 8/X, cybercriminals had already set up shop, hoping to exploit the hype.
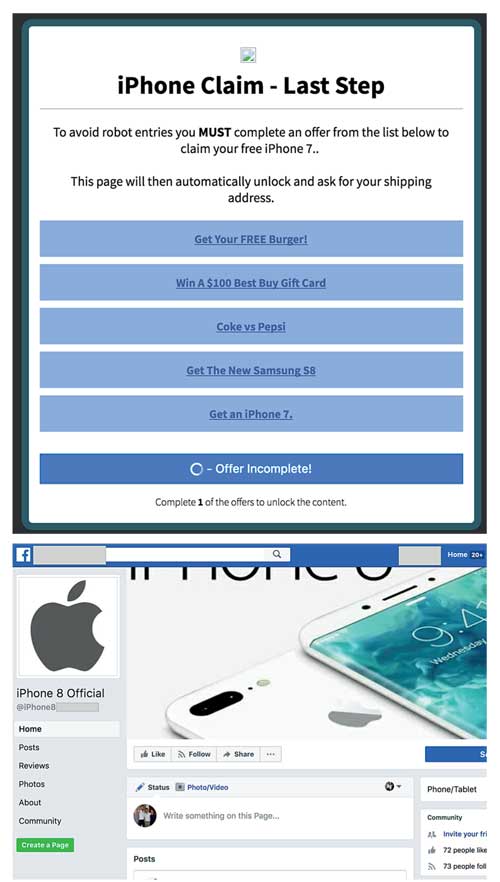
ZeroFOX Alpha Team reports an uptick in malicious content involving iPhones actively spreading across many popular social networks. Most of the attacks offer a “giveaway” of one of the new iPhones, encouraging victims to click a malicious link, follow a profile, like or share certain content, or submit personally identifiable information (PII). The high price tag of the new devices, between $699 to $999, together with the trustworthy Apple brand, makes this type of social engineering attack particularly dangerous to the average social media user.
The automated ‘ZeroFOX Platform’ has identified 532 fraudulent iPhone social accounts and counting, most of which take one of a few different forms:
- Fame farming is designed to rapidly gather large numbers of followers, likes and shares. Like in the example above, accounts can impersonate popular brands to piggyback off their perceived trustworthiness. After the fake account amasses enough digital popularity, it can be repurposed to launch larger attacks or commit other fraudulent activity. It also could be sold on the black market to other cybercriminals.
- PII harvesting is used to gather details that can be used to hack an account, socially engineer the victim at a later date, perform more elaborate attacks through other social and digital channels like email, or in the worst case: pull off identity theft. Dozens of these sites had similar redirect chains: first directing a user to a blog site, then redirecting to a fake survey which prompts users to enter personal details in order to claim their “free iPhone.” For an attacker, social media can be abused to create a variety of accounts to promote the same payload, increasing the surface area and total exposure of the attack. Moreover, linking and commenting between accounts can make them appear more trustworthy from the perspective of would-be victims.
- Phishing and malicious link distribution is a well-trodden social media attack that relies on attracting users to click through to external websites. This example uses the promise of a free iPhone to lure the user to click a URL that attempts to download malware-laden software on the victim’s machine. Websites like this trick users into believing that their software is out of date or scare them into believing their firewall has been disabled.
Scams like these are nothing new. Attackers regularly “newsjack,” tailoring their attacks to whatever is trending online and in the media, be it a holiday, the latest gaming fad, a new popular product or internet trend. Social media is abused by scammers to spread these attacks to the broadest possible audience, all while tailoring their group of targets using hashtags or abusing the publicly available follower list of popular brands, celebrities and other accounts. Scammers can rapidly segment their victim population, customise the attack, build fake accounts and launch their scam campaign at scale.
ZeroFOX Alpha Team recommends the following:
- Any account offering an iPhone giveaway may be fraudulent. Do not trust these accounts or the links they promote. Hover over URLs to get a preview and look closely for impersonator URLs with characters meant to look like others.
- Beware of brand impersonations. Unless it has the blue verified checkmark, do not click anything that accounts posts as it is likely an impersonation of the real profile.
- Scam websites often lack SSL (or TLS) web site certificates, which is standard for almost every website, especially those asking for credentials or credit card info. This has long been a method by which consumers can be assured that the site is legitimate and safe as demonstrated by the “https” designation, which many browsers display in green. If the site doesn’t have an SSL/TLS web site certificate and is not encrypting your information, it’s probably not safe to trust that site.
- Ensure two-factor authentication is enabled on your social media accounts when available. This provides yet another barrier of protection should a malicious page steal your credentials. Many social networks can now require a code be sent to your phone or via email when they detect a new browser or device attempting to access your account.
- Avoid downloading and installing apps or files you encounter on social media unless you verify they are trustworthy. Mobile apps should only be downloaded from curated app stores such as the Apple App Store or Google Play, and users should be very cautious when downloading apps from outside these marketplaces.
- Ensure that your anti-virus and anti-malware is kept up-to-date on your device, whether it’s a PC, Mac, or mobile device.
- Curate who you follow. Following suspicious accounts increases your chances of being exposed to scams, and even benign accounts can be hijacked by or sold to scammers.
- Above all be careful what you click on social media! If it looks suspicious, it may very well be.

