Wednesday Feb 25, 2026
Wednesday Feb 25, 2026
Monday, 22 April 2019 00:00 - - {{hitsCtrl.values.hits}}
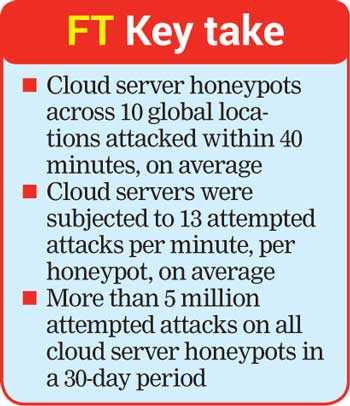
 Sophos (LSE: SOPH), a global leader in network and endpoint security, today announced the findings of its report, Exposed: Cyberattacks on Cloud Honeypots (accessible at http://www.sophos.com/CloudHoneypotsReport), which reveals that cybercriminals attacked one of the cloud server honeypots in the study within 52 seconds of the honeypot going live in Sao Paulo, Brazil. On average, the cloud servers were hit by 13 attempted attacks per minute, per honeypot. The honeypots were set up in 10 of the most popular Amazon Web Services (AWS) data centres in the world, including California, Frankfurt, Ireland, London, Mumbai, Ohio, Paris, Sao Paulo, Singapore, and Sydney over a 30-day period. A honeypot is a system intended to mimic likely targets of cyberattackers, so that security researchers can monitor cybercriminal behaviours.
Sophos (LSE: SOPH), a global leader in network and endpoint security, today announced the findings of its report, Exposed: Cyberattacks on Cloud Honeypots (accessible at http://www.sophos.com/CloudHoneypotsReport), which reveals that cybercriminals attacked one of the cloud server honeypots in the study within 52 seconds of the honeypot going live in Sao Paulo, Brazil. On average, the cloud servers were hit by 13 attempted attacks per minute, per honeypot. The honeypots were set up in 10 of the most popular Amazon Web Services (AWS) data centres in the world, including California, Frankfurt, Ireland, London, Mumbai, Ohio, Paris, Sao Paulo, Singapore, and Sydney over a 30-day period. A honeypot is a system intended to mimic likely targets of cyberattackers, so that security researchers can monitor cybercriminal behaviours.
In the study, more than 5 million attacks were attempted on the global network of honeypots in the 30-day period, demonstrating how cybercriminals are automatically scanning for weak open cloud buckets. If attackers are successful at gaining entry, organisations could be vulnerable to data breaches. Cybercriminals also use breached cloud servers as pivot points to gain access onto other servers or networks.
“The Sophos report, Exposed: Cyberattacks on Cloud Honeypots, identifies the threats organisations migrating to hybrid and all-cloud platforms face. The aggressive speed and scale of attacks on the honeypots shows how relentlessly persistent cybercriminals are and indicates they are using botnets to target an organisation’s cloud platforms. In some instances, it may be a human attacker, but regardless, companies need a security strategy to protect what they are putting into the cloud,” said Sophos security specialist Matthew Boddy. “The issue of visibility and security in cloud platforms is a big business challenge, and with increased migration to the cloud, we see this continuing.”
Visibility into weaknesses
Continuous visibility of public cloud infrastructure is vital for businesses to ensure compliance and to know what to protect. However, multiple development teams within an organisation and an ever-changing, auto-scaling environment make this difficult for IT security.
Sophos is addressing security weaknesses in public clouds with the launch of Sophos Cloud Optix, which leverages artificial intelligence (AI) to highlight and mitigate threat exposure in cloud infrastructures. Sophos Cloud Optix is an agentless solution that provides intelligent cloud visibility, automatic compliance regulation detection and threat response across multiple cloud environments.
“Instead of inundating security teams with a massive number of undifferentiated alerts, Sophos Cloud Optix significantly minimises alert fatigue by identifying what is truly meaningful and actionable,” said Sophos CISO Ross McKerchar. “In addition, with visibility into cloud assets and workloads, IT security can have a far more accurate picture of their security posture that allows them to prioritise and proactively remediate the issues flagged in Sophos Cloud Optix.”
Key features in Sophos Cloud Optix
Smart visibility – Provides automatic discovery of an organisation’s assets across AWS, Microsoft Azure and Google Cloud Platform (GCP) environments, via a single console, allowing security teams complete visibility into everything they have in the cloud and to respond and remediate security risks in minutes
Continuous cloud compliance – Keeps up with continually changing compliance regulations and best practices policies by automatically detecting changes to cloud environments in near-time
AI-Based monitoring and analytics – Shrinks incident response and resolution times from days or weeks to just minutes. The powerful artificial intelligence detects risky resource configurations and suspicious network behaviour with smart alerts and optional automatic risk remediation