Saturday Feb 21, 2026
Saturday Feb 21, 2026
Friday, 9 August 2019 00:00 - - {{hitsCtrl.values.hits}}
National security became a grave concern for Sri Lankan society after the Easter Sunday tragedy on 21 April. Even after passing the three-month remembrances just a few weeks ago, this concern and the associated anxieties have not yet come to a cease. This critical aspect of national security affects all other economic activities and the civil life of the population. 
Mitigating security risks and ensuring a sound security environment shall be the utmost responsibility of the Government. This article intends to describe several underlying principles that can be used to mitigate current security risks in our society. The principles discussed below are derived from the general risk mitigation philosophies used in industrial and societal safety management arena.
Management of 3Ss – Safety, Sustainability, and Security
Safety can be broadly defined as “freedom from unacceptable risk”. Therefore, the term “safety” encompasses a wide domain. However, in industrial safety management, the term “safety” is primarily used to describe the prevention of various technology and process related hazards such as fires and explosions initiating from industrial processes; leaking of dangerous chemicals, gases, and wastes; transport accidents, etc. These harmful incidents can be triggered due to inappropriate designs, non-optimum operating procedures, poor working conditions, inadvertent human errors, or sometimes due to natural events.
The term “sustainability” represents “environmental safety” aspects; mainly the pollution prevention (air, water, soil, ecosystems) and the sustainable use of resources (material and energy). Meanwhile, the dimension of “security” includes those aspects of safety threats emanating from deliberate manmade actions such as theft (physical materials as well as intellectual properties), vandalism, sabotage, and terrorism.
Management of Safety, Sustainability, and Security (3Ss) involve many analogous principles. These principles have been interwoven to formulate comprehensive 3S management systems adopted in many safety critical industries such as chemical processing, offshore petroleum, nuclear, aviation, etc. These industries must use such comprehensive and structured systems to manage safety, sustainability, and security. This is due to the tremendous consequences that could result in, if the conditions would go wrong at any time during their operations.
These industries have learnt vital lessons through catastrophic major accidents happened in the history. Bhopal chemical disaster (1984), Piper Alpha offshore oil platform fire (1988), Deepwater Horizon oil spill (2010), Chernobyl nuclear accident (1986), Fukushima Daiichi nuclear accident (2011), Malaysian Flight 370 air accident, Ethiopian Flight 302 air accident, and Algeria’s In Salah gas plant terrorist attack (2016) are a few example cases.
In fact, many such major catastrophes had been successfully used as the turning points in changing and improving entire 3S management systems in safety-critical industries. Therefore, it is high time to adopt analogous principles to formulate a national safety and security management program for Sri Lanka, by adopting well-structured and comprehensive methodologies already used in the industrial safety management field. The Easter Sunday tragedy, while it was devastating and dreadful, should still be used as an opportunity to build such a security management system, in order to prevent similar events from occurring in the foreseeable future.
The following is a simplified assessment of underlying safety management principles and their analogues applications in societal security risk management.
Threat recognition
Safety management begins with a comprehensive hazard recognition procedure followed by a risk assessment study. Hazards are the events or agents that can cause harm. In industrial safety arena, these can be various hazardous conditions such as the presence of high pressure, high temperature, or inventories of hazardous materials (i.e. flammable, explosive, or toxic substances).
When it comes to security management, the applicable security hazards, in other words “threats”, such as various types of terrorist attacks, sabotages, thefts, attacks against VIPs, etc. must be recognised. Irrelevant hazards may be eliminated from further assessments. For example, an attack against a particular VIP can be an applicable hazard. But, due to the existing security barriers around that VIP, the actual risk of a successful attack might be negligible. On the contrary, an attack against a commonly accessible religious worship place can be one hazard with significant risk.
Vulnerability and risk assessments
As briefly explained above, the presence of hazards does not necessarily mean that they pose a significant risk. “The risk” is defined as the product of the “consequences or the extent of the harm” and the “probability of occurrence”. For example, if “theft” is a relevant security hazard for a certain establishment (e.g. supermarket building), the probability of its occurrence can be high but the security consequences may not be that significant (even though economic consequences can be significant). Thus, the relevant security risk could be low. On the other hand, if we consider the event of a terrorist attack against a religious worship place, its probability of occurrence may be quite low (depending on the security environment) but if happens, its consequences will be grave; thus, the hazard of a terrorist attack may bear a high risk value.
On the other hand, a vulnerability is a certain character of a system (or an establishment) that can be (or will be) exploited by a particular security threat to cause harm. For example; any loopholes in a security procedure that can lead to increased probability of an attack. Another example is that a jewellery shop can be more vulnerable to theft compared to a grocery store because of the high value goods – if they both have similarly visible security arrangements. That means, the jewellery shop needs higher level of security measures to compensate for its increased vulnerability (or the increased risk).
Basically, vulnerabilities are either weaknesses or inherent characters that attract or facilitate specific security threats. Thus, high vulnerabilities can induce higher probabilities of security events, therefore leading to higher security risk levels. A vulnerability assessment must, therefore, be a part of probability assessment when determining the eventual risk level.
Accordingly, as the basis of any good security management program, a comprehensive assessment shall be conducted to identify the applicable hazardous events with a significant risk. Security hazards and risk assessments must be conducted by security experts in a systematic way using all available information at the time. It must take note that the security climate of a country can have rapid dynamics (even more so than in the industrial safety management). Therefore, the security risk assessments must be regularly updated to capture the changing security environment, with respect to both local and global events.
Security barriers and layers of protections
The intent of security barriers is to reduce the risk posed by identified threats. Like safety barriers in any safety-critical system, the security barriers protecting the national security must be multi-layered with a number of different techniques.
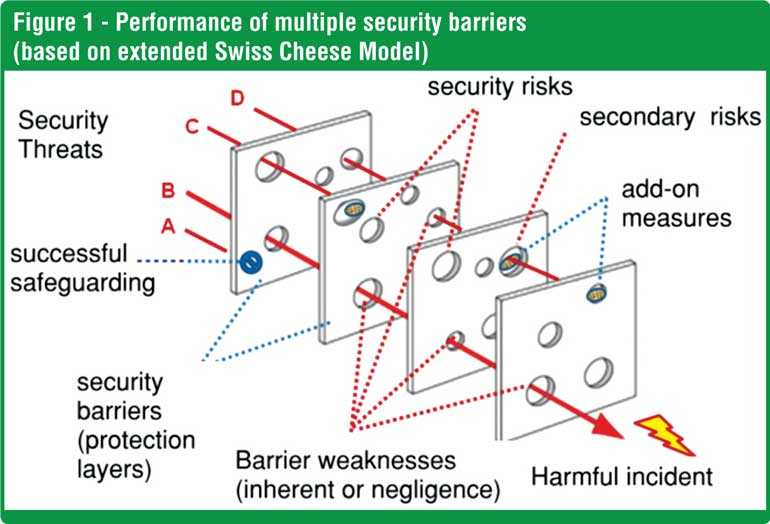
As shown in Figure 1 (known as the Swiss Cheese Model), a threat can transfer through several security barriers when their weaknesses /vulnerabilities (inherent or due to human failures) are aligned. However, the threat can be stopped by at least one security barrier that has no weaknesses (holes) aligned with the path of that threat. Further, at least several of the multi-layered security barriers shall also be independent from each other so that one common cause failure will not impact all barriers. Then, those barriers are called “independent security layers”. Manual intelligence gathering, electronic surveillance, physical presence of guards, vehicle checks and road barriers, metal/explosive detection techniques, etc. are some examples of the common security barriers that can be utilised.
Threat detection
In industrial safety systems protecting hazardous installations (such as oil and gas processing plants, nuclear power stations, etc.), various detection systems are used for the early identification of developing events/threats. Fire detectors, flammable gas detectors, toxic gas detectors, oil mist detectors, etc. are such detection devices that are installed at critical locations. They are supposed to trigger upon the earliest indication of a fire threat or a hazardous gas leak. Usually automated safety systems are then activated to either extinguish the fire and/or to nullify the threat by depressurising the whole plant (or a section of it).
Similarly, when it comes to national security, intelligence gathering is the most prominent way of early threat detection. Such mechanisms must always be at fully operational status and must be directed towards the particularly high threats recognised by security risk assessments.
Active and passive security measures
An active safety measure is something that can be immediately activated to safeguard against a developing threat. In a typical industrial safety apparatus, these active safety measures, such as firewater discharge, are often triggered by a threat detection (e.g. fire detection, gas leak detection). In a security environment, active security measures could include immediate deployment of troops to sensitive locations upon receiving intelligence. Further, active seeking and deactivation of threat elements must also happen (e.g. pre-emptive arrests).
The passive safety measures in industrial safety management means that certain barriers stand resistant to developing threats. These are not triggered by the threat but stand passively to deter the consequences of any eventual harm. For example, passive fire protection (PFP) or heat insulation of safety critical plant components (such as critical structural elements or safety valves) will help them survive longer when exposed to a fire, i.e. buying time until their safety function is carried out (e.g. evacuation of the plant, or depressurisation of the gas inventory).
In a security environment, passive security measures can be anything from a small security guard station or a checkpoint, to an explosion resistant building design. For example, during the Easter Sunday attack, it was later discovered that one suicide bomber had abandoned his attempt when he saw a few policemen at a church near Dehiwala (policemen were there for another purpose apparently).
Security/safety culture
The concept of “safety culture” is being promoted as a modern philosophy to encompass the entirety of a safety management system. The same concept can be used in security risk management as well. A society with a good security culture has a heightened security risk awareness throughout its domain. The security is regarded as everyone’s responsibility (not just the Government’s or the security forces’ responsibility). Such society will have a good alertness level, and a fast information exchange capability with respect to potential threat elements. Meanwhile, the society stays calm and avoids chaos.
Creating a good security/safety culture within a society needs efforts and time. It requires a large commitment from the political leadership; and also the education system has a significant role to play. An existing security/safety culture can always be improved; and in the meantime it takes continuous efforts to maintain it at a good level. If continuous improvements are not made, it’s all natural that an existing good security culture can be eroded over time (perhaps that has been seen in SL too).
However, once a good security culture is established and maintained, it makes very difficult for threat actors to play freely within such a society. Even if they succeed in plotting a successful security breach, its eventual success rate can be greatly compromised by the inherent resistance of a society with good (positive) security culture.
Security scenarios and the dimensioning security events
Another important concept stemming from industrial safety management is to define various significant security scenarios that can be expected within a certain security perimeter (e.g. a city or a town, or the whole country). Simultaneously, the size or the expected extent of each scenario must be estimated. For example, if suicide bomb attack is recognised as a potential security scenario, it should be evaluated the possibility of simultaneous attacks at multiple locations.
When defining such scenarios, the attention is normally put on the applicable security threats (relevant hazards); but should not count on the successful deployment of all security barriers. This is because, if all the security barriers are working as they are intended, then the dimensioning security events will be almost non-existent. That is not the purpose of defining dimensioning security events. We need to comprehend dimensioning security events as the potential ultimate consequences of the credible security threats, if one or more security barriers should eventually fail. And more importantly, we need to recognise dimensioning security events in order to formulate a comprehensive emergency response and crisis management plan.
Emergency response and crisis management
As briefly indicated before, irrespective of the security barriers in place, a country’s (or an organisation’s) security management system must incorporate a comprehensive emergency response and crisis management plan. This plan must include detailed information on how to respond to the defined dimensioning security events within the shortest possible time and with maximum mitigation effect.
The plans for rapid force deployment, containment of the evolving event, handling and transporting the injured personnel/casualties, emergency communication, spare capacities of the hospitals, are some of the important aspects that must be well planned for. It is highly important to establish special emergency communication networks that can be used during emergencies (e.g. a few emergency communication telephones must be available at each Grama Niladhari division, or at critical locations within a certain area).
As seen during Easter Sunday attacks in SL, it is typical that regular telephone networks breakdown due to overload, and therefore such communication networks cannot be relied upon for emergency communication. Due to the lack of such communication means, apparently the number of casualties had been increased at the targeted churches located outside of Colombo city.
It was also clear that the major hospitals in and around Colombo had not been prepared for any contingency. Due to the large patient flow, some of the critically-injured personnel had to be land transported to hospitals located as far away as Karapitiya, Galle. If there was an analysis of dimensioning security events, and a crisis management plan for the expected consequences (e.g. no. of casualties), there should have been a spare capacity reservation in the major hospitals around Colombo that can be rapidly mobilised to action within a very short time period.
Final outlook
As we have just passed the three months mark since the tragic events that befell Sri Lanka on 21 April, it is definitely an appropriate time now to look at the broader picture and try to comprehend the full perspective.
It should be noted that one of the most important aspects of a good security culture is to learn valuable lessons from past events and never allowing to repeat the same mistakes. A good security/safety culture is a learning culture, instead of being a blaming culture. It is more important to understand what went wrong than who did wrong.
Therefore, it is highly recommended to adopt some of the key safety (3Ss) management principles used in safety critical (high risk) industries, to formulate an all-inclusive and fully comprehensive security management program for the country. Such a program must address various technical, demographic, geopolitical, social, and psychological dimensions of the relevant security threats. The threats must then be risk assessed; and a risk-based methodology must be used to formulate and implement necessary security barriers. A comprehensive emergency response and crisis management plan must also be followed.
More importantly, the security management plan must be agile (adaptive) and dynamic; that means it must be regularly updated and adopted to the ongoing risk picture in the country, region, and the world. If such a systematic program is followed hereafter, it will not be an insurmountable challenge to avert future threats (seen or unseen) to the public safety and national security of Sri Lanka.
[The writer, Ph.D. (NTNU), M.Sc.Tech. (USN Norway), M.Sc. &B.Sc.Eng.(1stHons) (UoM), AIChE, AMIE(SL), is currently consulting for the Norwegian petroleum industry, within his field of expertise of safety engineering and management. The key areas of his industrial experience and research interests include process safety and safety barriers design, sustainability and industrial safety risks management, and safety culture. He can be reached via email at [email protected].]